j_k_redtail
Member
I'm posting this mostly as a Public Service Announcement. Did a search, saw nothing.
Here is a video demonstrating an infection on a test machine.
And here are some user experiences:
This thing has been around for a little over a month but it has exploded in the last few days. This is not your average ransomware: it will encrypt files on network shares and external drives, so keep that in mind if that's your backup strategy. Yes, you will lose the files if you don't pay. The family IT guy will not be able to break the encryption and recover them.
These things are only going to get more sophisticated. You can have the best security software in the world, but remember: the user is usually the weakest link. Remind people in your life who use technology to watch what they click.
Edit:
Edit 2: Virus scanners which will detect cryptolocker:

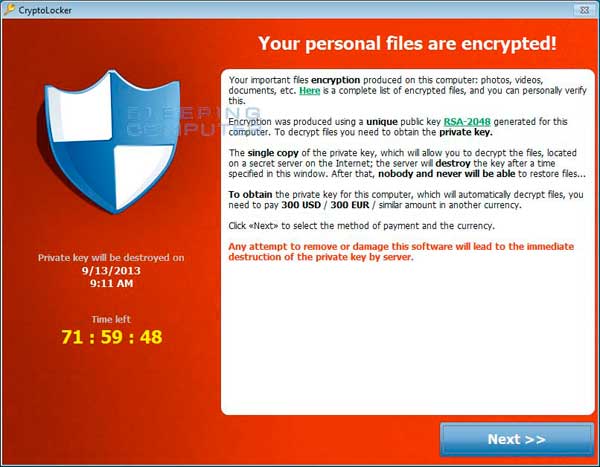
CryptoLocker is a ransomware program that was released around the beginning of September 2013. This ransomware will encrypt certain files using a mixture of RSA & AES encryption. When it has finished encrypting your files, it will display a CryptoLocker payment program that prompts you to send a ransom of either $100 or $300 in order to decrypt the files. This screen will also display a timer stating that you have 96 hours, or 4 days, to pay the ransom or it will delete your encryption key and you will not have any way to decrypt your files. This ransom must be paid using MoneyPak vouchers or Bitcoins. Once you send the payment and it is verified, the program will decrypt the files that it encrypted.
Here is a video demonstrating an infection on a test machine.
And here are some user experiences:
Here's my situation: Client has 4 computers connected to a Synology NAS (uses Linux I believe) to share files. One of the clients got the Cryptolocker virus through an email attachment. Files on both the one client computer and the shared files on the NAS were encrypted. Backups were no good, so the $300 ransom was paid. The payment happened just before closing time and the computer was left on overnight.
Returning in the morning, found that all the files on the infected client were decrypted but none on the NAS. Curiously, a file named "PrivatKey.bin" was left on the desktop.
I am seeking information on how to re-start the decryption or maybe to use that PrivatKey.bin file for decryption if anyone has ideas.
....
PS we paid. $300 for 14,400 files returned, 11 years of (then) non-backed up data. It took two hours for the decryption process to begin, and another 3 or so for it to finish. Client and staff grateful and overjoyed. Very Stockholm Syndrome. Not mad at attacker at all, just grateful the beating had stopped.
...
Cryptolocker hit us 2 days ago and we have been fighting it since. Just wanted to run through what we have tried in hopes that it might help others. I know paying these guys is a tough call to make but when you are faced with losing 40,000 files you do what you have to. We ran malwarebytes and removed cryptolocker before we realized we needed it to pay these guys off for the data to be decrypted so we spent all day yesterday trying to reinfect using the original email that was clicked on to infect the PC in the first place....
This thing has been around for a little over a month but it has exploded in the last few days. This is not your average ransomware: it will encrypt files on network shares and external drives, so keep that in mind if that's your backup strategy. Yes, you will lose the files if you don't pay. The family IT guy will not be able to break the encryption and recover them.
These things are only going to get more sophisticated. You can have the best security software in the world, but remember: the user is usually the weakest link. Remind people in your life who use technology to watch what they click.
Edit:
http://www.reddit.com/r/sysadmin/comments/1mizfx/proper_care_feeding_of_your_cryptolocker/
Yeah, Reddit, but that's a good link to read about the malware. Lots of useful information.
something for the OP•We have confirmation that both Malwarebytes Antimalware Pro and Avast Free and Pro will stop CryptoLocker from running. My personal choice of the two is MBAM Pro but research on your own, AV Comparatives is a wonderful resource.
Edit 2: Virus scanners which will detect cryptolocker:
I've just uploaded a sample of this malware to Virustotal (it scans the file with a bunch of different AV engines and tells you if they detect the file). The results are here:
https://www.virustotal.com/en/file/...0a3c34fc2008e210ccfe6dae/analysis/1382805599/
Pretty much every AV, provided you have the latest updates, will detect it.
