Apple released a new iOS update yesterday. Initially, it seemed like a very minor update, and the change log was very brief:
It turns out, this update fixes a major security flaw in the operating system that exists on both iOS and OSX. Apple promised a fix soon for OSX.
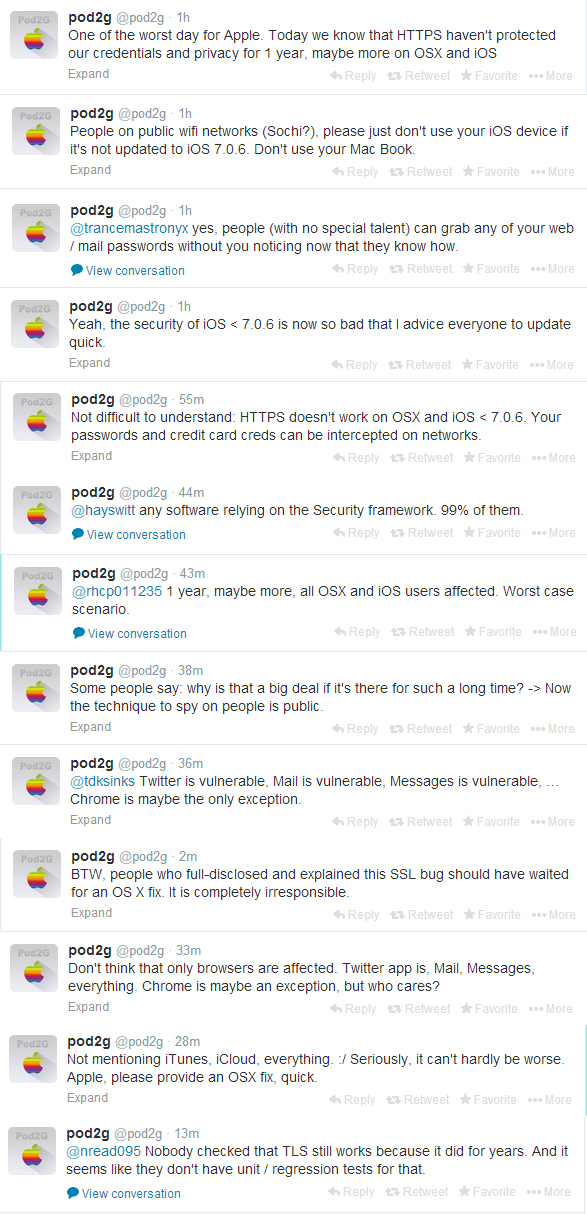
Here's what Pod2G (security researcher/major contributor to iOS jailbreaks) had to say about this (read from top to bottom):
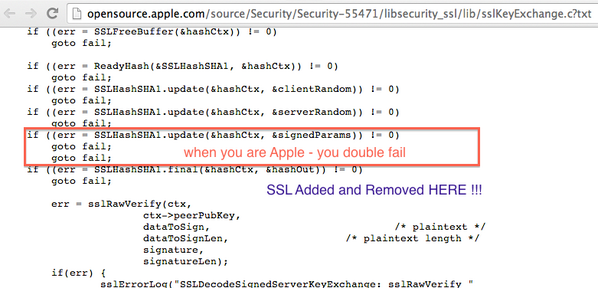
Here's a technical write-up of why this is bad, linked to by Pod2G
This security update provides a fix for SSL connection verification.
It turns out, this update fixes a major security flaw in the operating system that exists on both iOS and OSX. Apple promised a fix soon for OSX.
Here's what Pod2G (security researcher/major contributor to iOS jailbreaks) had to say about this (read from top to bottom):

Here's a technical write-up of why this is bad, linked to by Pod2G