-
Hey, guest user. Hope you're enjoying NeoGAF! Have you considered registering for an account? Come join us and add your take to the daily discourse.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Major security flaw in iOS and OSX, be sure to update to iOS 7.0.6 ASAP
- Thread starter PFD
- Start date
- Status
- Not open for further replies.
how did this get missed upon review? I'm assuming that code gets reviewed by multiple senior staff before it's given the green light..
Hipsters don't like braces! ;-)
It enters fail: before hitting the conditional, which will always return true.
Which iOS are you on? iOS 6 should be updated to 6.1.6. If you're <5, you're okay.
edit: For those of you just joining us, please use https://gotofail.com/ to see if your system is compromised. Chrome is not affected because it uses its own verification system.
I have a rMBP on mavericks. I only ever use firefox and chrome, only safari as a fallback for any site that isn't working on the other two for whatever reason (aka very rarely), am I safe until the patch? rMBP doesn't have an ethernet port either, and I don't own the dongle that adds that functionality.
GravityMan
Member
Brackets.
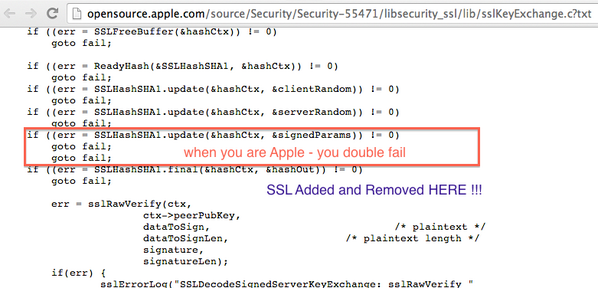
Looks like a simple oversight (copy-paste error) that unfortunately occurred in a very, very bad place. Apple might want to reevaluate their code inspection and QA routines, especially in their security modules. Of course, bugs can still slip through even if testing procedures are rock solid.
Also look at the indentation issues... any code review should have raised red flags around this code.Looks like a simple oversight (copy-paste error) that unfortunately occurred in a very, very bad place. Apple might want to reevaluate their code inspection and QA routines, especially in their security modules. Of course, bugs can still slip through even if testing procedures are rock solid.
Hmm, I have an 8gb iPhone 4 which means I actually have 6.3gb of space. The update requires 3.7gb free space. I currently have 1.2gb. Any advice on how to free up some space short of deleting all my photos (which total 1gb) and apps?
Your best bet would probably be to backup your phone on a PC, restore through itunes to 7.0.6, then restore your data from backup.
Be sure to transfer your apps through iTunes first if you don't wanna redownload them.
edit: try updating through iTunes first as Guess Who suggested below. It would save you a lot of time if it works
Hmm, I have an 8gb iPhone 4 which means I actually have 6.3gb of space. The update requires 3.7gb free space. I currently have 1.2gb. Any advice on how to free up some space short of deleting all my photos (which total 1gb) and apps?
Update via iTunes instead of over-the-air and you won't need to free up space.
Hilarious, that's exactly why beginners programming classes usually tell students to always use brackets, even when they aren't needed.
What's unsettling tough is that Apple apparently doesn't write tests for their code, otherwise this would have been caught within minutes. And they could also do with some basic coding standards, that file is all over the place: Different spacing, brackets are used inconsistently and often end up on the same line, except when don't. Sometimes else goes after the closing bracket, sometimes on a new line and sometimes two lines below.
Doesn't exactly give you confidence in their software, given that iOS has actually been their focus since OSX 10.5.
What's unsettling tough is that Apple apparently doesn't write tests for their code, otherwise this would have been caught within minutes. And they could also do with some basic coding standards, that file is all over the place: Different spacing, brackets are used inconsistently and often end up on the same line, except when don't. Sometimes else goes after the closing bracket, sometimes on a new line and sometimes two lines below.
Doesn't exactly give you confidence in their software, given that iOS has actually been their focus since OSX 10.5.
I have a rMBP on mavericks. I only ever use firefox and chrome, only safari as a fallback for any site that isn't working on the other two for whatever reason (aka very rarely), am I safe until the patch? rMBP doesn't have an ethernet port either, and I don't own the dongle that adds that functionality.
That's what I don't know. For iOS, it's straightforward because everything but Chrome uses Apple's SSL handling. For OSX, I have no idea since I'm not sure what else depends on it.
Check both FF and Chrome on that website. If they're secure, then I'd assume that any traffic going through those is good, but anything else is bad.
You are already a recipient of a lump sum from a Nigerian prince.So I've updated.
Now what? Change all passwords for everything and get new credit cards?
Update via iTunes instead of over-the-air and you won't need to free up space.
Thanks! I'll give it a try tomorrow morning.
So what does this mean for the previous year? Change passwords? Like for emails and AppleIDs? Or has the information come and gone?
What about users who use 3G data? I guess the carriers will have 'privileged network positions'?
For the security thing, is it mainly for public wifi where it's an issue? Am I in trouble if I haven't used any in a while?
How you connect to the internet is irrelevant. Anyone along the chain could see your communications in plaintext.
helloresolven
Member
How you connect to the internet is irrelevant. Anyone along the chain could see your communications in plaintext.
What? No they couldn't. You were vulnerable to a MITM attack. Your communications were still encrypted, but in certain cases it was possible to pass off a certificate without having to prove that you actually owned the private key behind it.
And it appears to only affect iOS/OS X when HTTPS/SSL was connecting to an IP address instead via a domain.
What? No they couldn't. You were vulnerable to a MITM attack. Your communications were still encrypted, but in certain cases it was possible to pass off a certificate without having to prove that you actually owned the private key behind it.
And it appears to only affect iOS/OS X when HTTPS/SSL was connecting to an IP address instead via a domain.
MITM = "anyone along the chain". As I understand, the bug is it turned off encryption entirely.
Phoenician_Viking
Banned
Dammit. Patch up emails iCloud and iMessages ASAP Apple you fuckers.
lastflowers
Banned
wow.
How you connect to the internet is irrelevant. Anyone along the chain could see your communications in plaintext.
Than how come on one of the links about this security flaw it states this
"To pull off the attack an adversary has to be able to Man-in-The-Middle (MitM) network connections, which can be done if they are present on the same wired or wireless network as the victim. Due to a flaw in authentication logic on iOS and OS X platforms, an attacker can bypass SSL/TLS verification routines upon the initial connection handshake."
Maybe I don't understand this tech speak but from what I quoted above it seems like if my home network is only used by me I am fine?
HUELEN10
Member
It's no downgrade, 7 runs great on a Mini.But I don't want to downgrade to iOS 7 on my OG iPad mini!
Than how come on one of the links about this security flaw it states this
"To pull off the attack an adversary has to be able to Man-in-The-Middle (MitM) network connections, which can be done if they are present on the same wired or wireless network as the victim. Due to a flaw in authentication logic on iOS and OS X platforms, an attacker can bypass SSL/TLS verification routines upon the initial connection handshake."
Maybe I don't understand this tech speak but from what I quoted above it seems like if my home network is only used by me I am fine?
Goddamnit, I goofed.
Sorry.
Phoenix
Member
Looks like a simple oversight (copy-paste error) that unfortunately occurred in a very, very bad place. Apple might want to reevaluate their code inspection and QA routines, especially in their security modules. Of course, bugs can still slip through even if testing procedures are rock solid.
Though a developer practice that made you put in braces would have made the error substantially more likely to find. I've never understood the desire to not have braces that seems to be growing ever prevalent in software development.
infiniteloop
Member
What is the oldest iOS release that is impacted by this bug?
iOS 6
Shit. My iP4 can barely handle iOS 6. I wasn't planning on upgrading until the iPhone 6 and iOS 8 came out later this year.
Same here, this fucking blows.
ALL of iOS 6? Thanks. I have family running iOS 6 on 3GSs.. Didn't see that there was an iOS 6 patch out, too.iOS 6
Alx
Member
Though a developer practice that made you put in braces would have made the error substantially more likely to find. I've never understood the desire to not have braces that seems to be growing ever prevalent in software development.
That's probably to reduce the number of lines in a program, and have as much information as possible in a single page. The same reason that makes people place opening braces at the end of a line instead of the beginning of the next one (I hate that convention btw, the symmetry between opening and closing braces should be kept, and I'd rather scroll a bit more)
vagabondarts
Member
So do I have to change all my passwords now? Please forgive me for not fully understanding the extent of the exploit... Could the information transmitted have been recorded?
Then they were all over the place ... We will probably see that side soon.
They are. The vision caster is gone. Coasting also happened at the Disney Company after Walt Disney passed away.I don't get what is going on at Apple any more.
Their product releases have slowed, their software releases have slowed and are more and more superficial, brain dead flaws like this slip through the cracks for 2 years, what is going on? It's like they're coasting.
Then they were all over the place ... We will probably see that side soon.
Same here, this fucking blows.
iPhone 4 runs great on iOS 7 if you take the simple step of turning on 'reduce motion' from the accessibility menu in settings/general.
Don't Laugh
Banned
I am fairly new to this jailbreaking, but do I update via itunes or OTA? and then do a full restore?
Do I have to "unjailbreak" before I update?
restore via iTunes and then jailbreak again
Intheflorsh
Banned
HTTPS doesn't work for an entire year and no one knew? This might be one of the biggest tech fuck ups I've ever heard about, holy shit.
iPhone 4 runs great on iOS 7 if you take the simple step of turning on 'reduce motion' from the accessibility menu in settings/general.
Jailbreaking and installing NoSlowAnimations and iCleaner helps a lot too
HTTPS doesn't work for an entire year and no one knew? This might be one of the biggest tech fuck ups I've ever heard about, holy shit.
I don't think this is the case. SSL connections were still encrypted/signed, just the certificate chain is always treated as valid, whether or not it was. This allows a MITM attack, because the public key used for encryption/signing may not be from the actual site.
CrudeDiatribe
Member
MITM = "anyone along the chain". As I understand, the bug is it turned off encryption entirely.
No, the traffic is still encrypted, it's that the Mac/iOS browser doesn't know who it's encrypting traffic to.
A man in the middle attack requires effort by an attacker to set up an intermediary network device (typically a router, though you could do it with a bridge), to intercept traffic between two hosts and re-write traffic in each direction so that the interceptor can read it and the participating parties don't realize it.
Alice thinks she's talking directly to Bob, and Bob thinks he's talking directly to Alice, but really they're both talking to Charlie who's helpfully passing the messages on after reading them.
The purpose of the SSL stack is to verify the identities of Alice, or Bob, or both. This code block is to prevent the traffic from flowing if there's a failure, which it doesn't do, due to the bug.
Aside from home/work networks, most people (not on the NSA payroll) do not have access to the infrastructure to implement such an attack.
The tweets in the OP suggesting people on free WiFi are at risk is misleading— someone just watching the traffic can't sniff your encrypted traffic even with this bug. Instead, you shouldn't be on any home or office network for which you don't know/trust the router owner.
TheGravemind
Banned
jesus christ
techgaf explain explain: is this vulnerability valid only if you use public network or hacker can use it in every condition ?
techgaf explain explain: is this vulnerability valid only if you use public network or hacker can use it in every condition ?
Thank you, nice explanation.
CrudeDiatribe
Member
is this vulnerability valid only if you use public network or hacker can use it in every condition ?
See my post above yours. I would assume the NSA or your country's equivalent has been reading your traffic since the fall of 2012; aside from that it's whether you trust the owner/IT staff of the local networks you're on. Whether the wifi network is open or encrypted makes no difference.
SteveMeister
Hang out with Steve.
This kind of bug can be very hard to find. It doesn't manifest itself as an error. If it's not caught when it's checked in, chances are it won't be caught for a long time, if at all. And indeed it's apparently been there since at least IOS 6. It's an easy mistake to make, and insidious because it can be hard to find.
That said, a static analysis tool or even a strict compiler would have caught it, warning that the code trailing the second goto was unreachable. Apple needs to make sure all their code is run through static analysis and they should also make all compiler warnings errors. Either would have prevented this.
That said, a static analysis tool or even a strict compiler would have caught it, warning that the code trailing the second goto was unreachable. Apple needs to make sure all their code is run through static analysis and they should also make all compiler warnings errors. Either would have prevented this.
Buggy Loop
Member
When will the maverick patch go online?
When will the maverick patch go online?
irregardless of this situation, is 10.9.2 long overdue now? I'm on a brand new rMBP and I'm a bit disappointed at times with the Finder crashing. Haven't lost any work (I use Adobe CC every day) and I haven't had a crash or hardlock up, but still.
- Status
- Not open for further replies.
